
The advent of digital currency has just assured one thing: whoever possesses the keys possesses the coins. A crypto wallet is more than just a repository—it's what gives consumers total control over their cryptocurrency. Without it, coins on exchanges are susceptible to hacking, platform collapse, and restrictions.
Security issues are not abstract. Crypto scams and theft stole more than $1.8 billion in 2024, with the majority attributed to hacked wallets or exchange hacks. Meanwhile, adoption continues to rise. As of mid-2025, more than 575 million individuals worldwide owned cryptocurrency, nearly double the figure two years prior. As new entrants join the space, secure and trustworthy storage has never been more essential.
This manual addresses how wallets function, the kinds available, and how you can protect your assets. You'll learn:
By the end, you’ll have a clear picture of how to store crypto safely and avoid common mistakes that cost investors money every year.
A wallet is a software program that enables you to store and manage your holdings of cryptocurrency. It is not like a wallet containing cash in your pocket: it does not hold coins. What it holds are the private keys that give you access to your assets on the blockchain. Whoever has those keys controls the assets.
Essentially, a wallet does two things:
With no wallet, there is no practical way to send, receive, or keep cryptocurrency by yourself. Keeping assets solely on an exchange is risky because you are trusting your assets with a third party. With an individual wallet, there's real ownership.
Short story: Cryptocurrency wallets are the middleman between you and the blockchain. They do not hold your coins but guard the digital keys that allow your assets to be accessed and stored.
To understand how wallets operate, it is helpful to know what exactly they hold. A wallet does not hold coins in it. Instead, it holds the keys that allow you to access coins recorded on the blockchain.
It's a difference that makes a difference. Public keys are open, but private keys are to be kept secret at any cost.
Your wallet address is generated based on your public key. It looks like an extended series of numbers and letters, like:
1BvBMSEYstWetqTFn5Au4m4GFg7xJaNVN2
The address instructs the blockchain where to send coins, but only its corresponding private key can release them.
An exchange account, however, doesn't allow access to private keys. The exchange will possess them and only credit balances against your account. This is easy but requires you to rely on the exchange to hold your money securely.
When sending crypto:
All of this happens in the background within seconds, but the security depends on your private key being safe.
Crypto wallets are of many types, and all weigh convenience against security differently. Which is most suitable is a function of how frequently you buy/sell, how much you have on deposit, and how much risk you're able to tolerate.
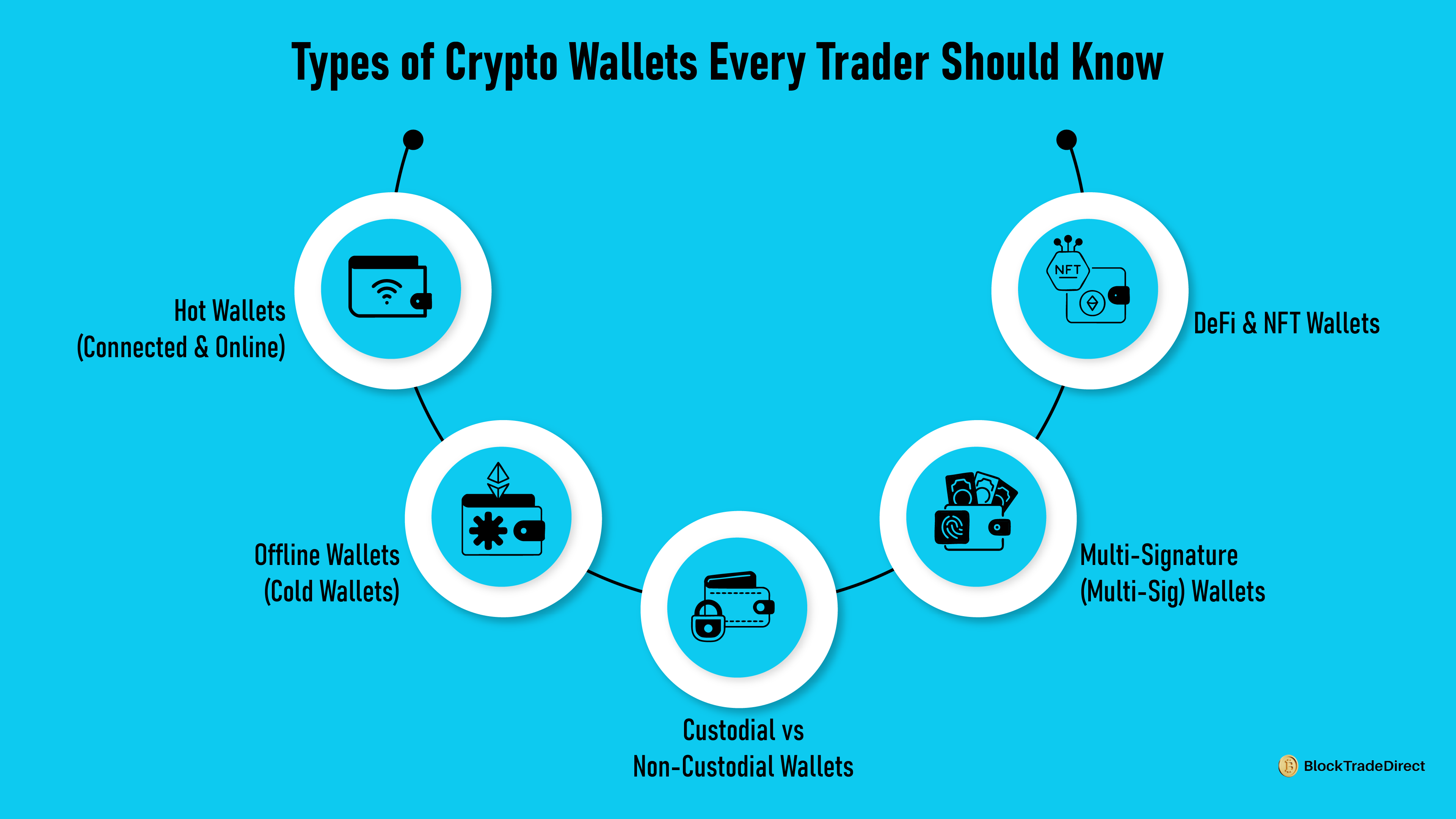
Hot Wallets (Connected & Online)
Hot wallets are connected to the Internet and are thus instantly usable but vulnerable to hacking. They are overwhelmingly most commonly software-based. Since many wallets connect directly with exchanges, it’s important to understand centralized vs decentralized exchanges.
Examples
Advantages
Disadvantages
Cold wallets keep keys offline to minimize vulnerability to online attacks. They're best used by long-term holders.
Types
Pros
Cons
Wallets that require more than a single signature key to authenticate a transaction. For instance, 2 of 3 registered signers must sign prior to spending money.
Best for
Decentralized finance and digital collectible wallets have distinct wallets of their own.
Cryptowallets are more than just storage. They give access to a variety of methods of utilization of virtual assets, depending on whether you keep long-term positions, make active trades, or interact with decentralized applications.
For long-term holders, the most secure is cold storage—specifically, hardware wallets. Offline storage of keys secures them against malware attacks and phishing. This is usually thought to be the optimal method of storing crypto in the long term, especially when considering larger positions.
Hot wallets are a good fit when you're buying and selling frequently. Because they're online and linked to dApps and exchanges, it happens fast. Security is the compromise, so they're only a good fit when you're dealing with small amounts that you'll be moving frequently.
Connected to DeFi platforms through DeFi wallets, users can stake tokens, lend cryptocurrency, or offer liquidity to earn a return. Browser extension wallets such as MetaMask are quite common.
NFT wallets are digital artwork, music, or game asset storage and administration systems. Moreover, they provide direct access to platforms such as OpenSea, Magic Eden, or Blur and consequently make purchases and sales of collectibles and view collectibles.
Peer-to-peer transfers are best enabled by mobile cryptocurrency wallets. They enable near-instant transfer of value from one country to another without going through traditional banking systems that come with their fees and delays.
Multi-signed wallets give extra protection to organizational funds as well as group initiatives. By insisting on a series of approvals before fund transfers may occur, they minimize risk from insider abuse or lost keys.
With true crypto thefts and scams continuing to accumulate billions annually, wallet security is not a neutral luxury. It's the keystone to safeguarding your investments. A wallet only holds as much as the manner in which you secure its keys, backups, and devices.
When setting up most wallets, you’re given a seed phrase (usually 12–24 random words). This phrase can restore your wallet if your device is lost or damaged. It also represents full access to your funds, so protecting it is critical.
Do’s
Don’ts
For more significant-value storage, multi-signature (multi-sig) wallets provide additional security. Rather than a single private key, they use multiple approvals to transfer funds. Even if compromised, attackers can't take action alone.
Best for
Because the majority of attacks are against compromised devices or networks, it is as crucial to keep your environment clean as your wallet.
Custodial wallets are FDIC-insured, while traditional bank accounts are not. Crypto wallets, however, are not. If money is stolen from a non-custodial wallet, recovery is nearly impossible. Some custodial wallets do have insurance against hacks or theft. Terms of coverage are highly variable, so always check the fine print.
Regulatory action is growing in the United States, particularly around custodial services. But for individual wallets, security is ultimately in their hands.
Not all wallets are created for the same reason. The appropriate one will depend on what you intend to do with crypto, your level of security comfort, and how much risk you are willing to assume. If you’re actively involved in crypto trading and investment, choose a wallet that matches your style and security needs.
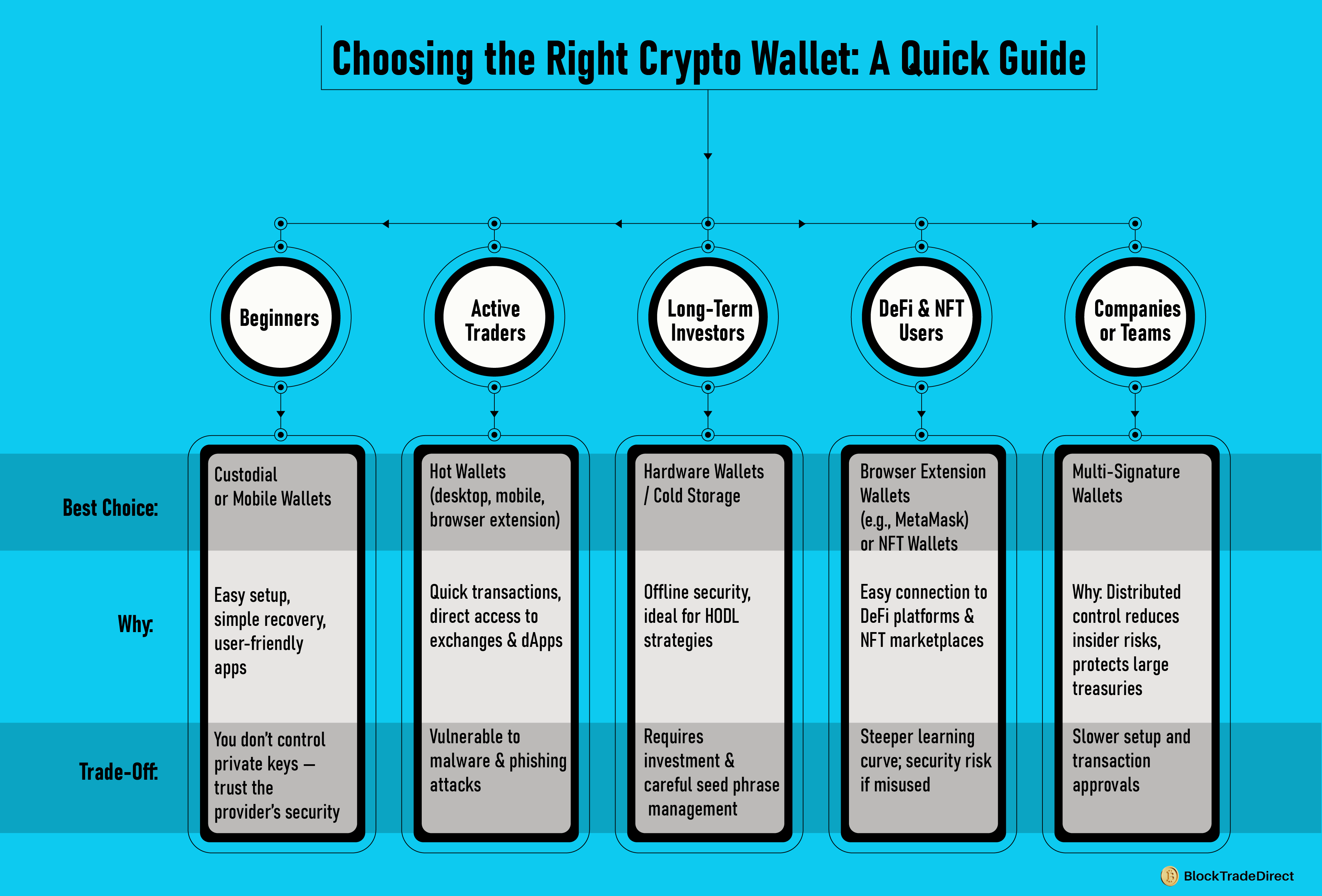
Beginners
It is not difficult to store crypto securely, but it does need discipline and adherence to simple steps. Here is a useful guide to safeguard your assets:
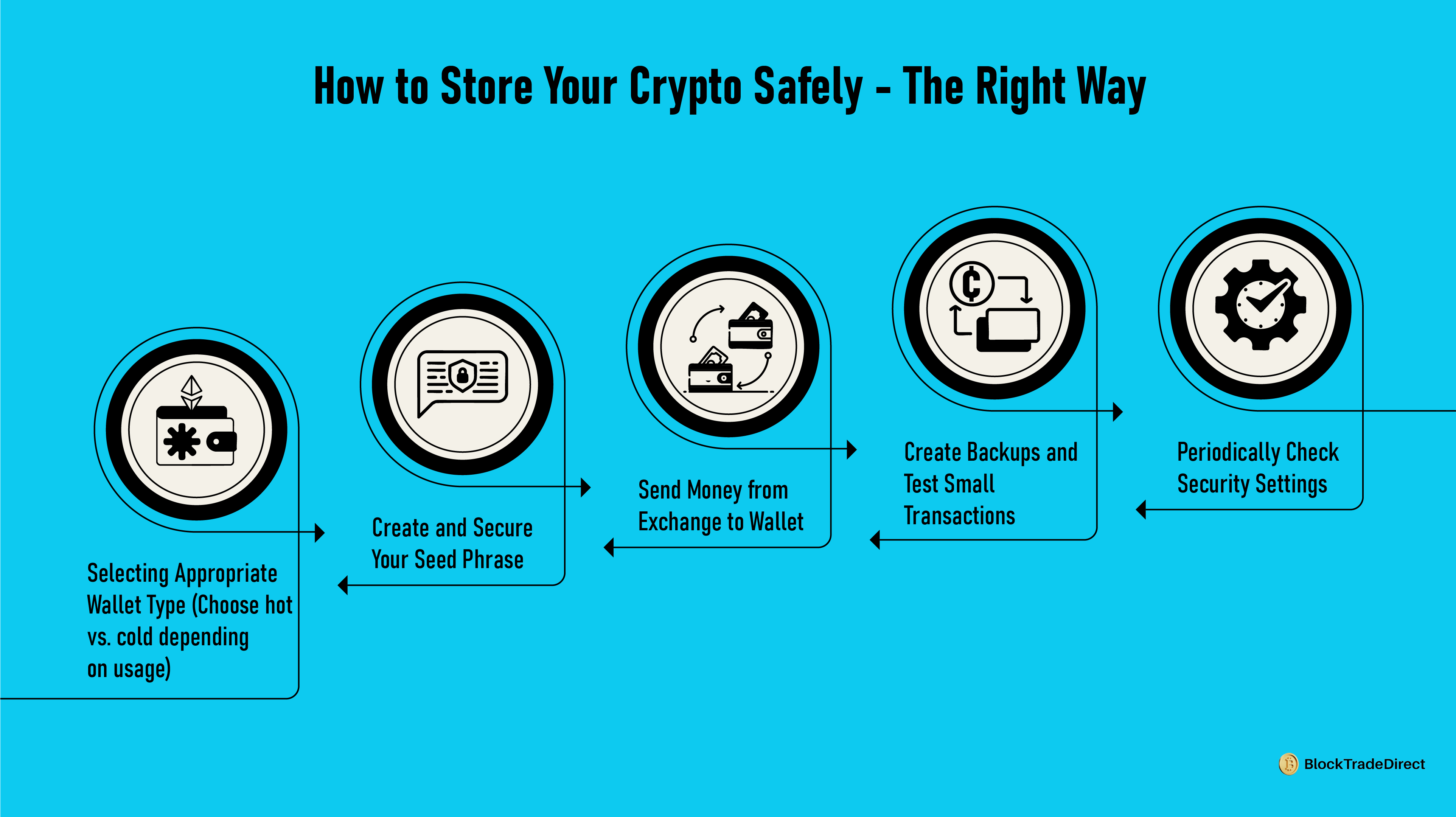
1. Select the Appropriate Wallet Type
Following these steps helps mitigate the most common causes of crypto loss, from hacks to human error. Along with wallets, practicing safe crypto trading in the USA is essential to protect your assets.
Even experienced users make minor errors that expose their cryptocoins to risk. Do not make these easy mistakes:

Being aware of these mistakes and consciously avoiding them is one of the simplest ways to make your crypto more secure.
There are many misconceptions regarding crypto wallets that can deceive newcomers as well as regular users. Eliminating them contributes to safer usage.

Most people think that having crypto on an exchange renders it a wallet that they own. Reality is that exchanges actually have your private keys. When a platform is hacked or becomes unavailable, your money is lost. Ownership is only realized when you have a wallet where you own the keys.
While hardware wallets have good protection offline, no hardware wallet is completely unbreachable. They are vulnerable to attack through social engineering attacks or accidental compromise of seed phrases, or even through phishing. Security is device protection along with responsible key handling.
Hot wallets are safe enough to do most tasks when done properly. Cell phone and computer wallets are secure when you have strong passwords, 2FA, and safe computers. They're good to use for users or traders who need constant access.
It is a loss-incurring recipe to leave out backups. When a device is stolen, lost, or crashes, your money could be lost forever. Always keep a number of safe seed phrase backups.
Others have different functions: hot and cold wallets, custodian and non-custodian, multi-sig or specialty DeFi/NFT wallets. Making a wrong choice could sacrifice convenience or security.
Awareness of such myths helps users make better-informed decisions and prevent costly blunders that could cost millions of dollars.
Comparison Table: Types of Wallets at a Glance
|
Wallet Type |
Key Feature |
Best Use Case |
|
Mobile Wallet |
Hot, non-custodial, supports DeFi/NFTs, instant access |
Daily transactions, trading small amounts |
|
Desktop Wallet |
Hot, non-custodial, secure on PC, multi-crypto support |
Trading and portfolio management |
|
Browser Extension Wallet |
Hot, non-custodial, connects with DeFi platforms and NFTs |
DeFi and NFT interactions |
|
Hardware Wallet |
Cold, non-custodial, strong offline security |
Long-term storage, high-value crypto |
|
Paper Wallet |
Cold, non-custodial, fully offline, QR code backup |
Ultra-secure backup or offline storage |
|
Custodial Wallet |
Cold, non-custodial, fully offline, QR code backup |
Beginners, small balances, convenience users |
|
Multi-Signature Wallet |
Hot/Cold, non-custodial, multiple approvals required |
Businesses, teams, large treasuries |
Additional Notes:
Crypto wallets are more than a tool to store your assets-they're the door to having real ownership of your assets. Decisions about which wallet to use depend upon convenience as much as security, so knowing something about hot, cold, custodial, and non-custodial wallets is a must.
Safe storage starts with:
By adopting these habits, you lower your risk of loss through hacks, human error, or lost credentials. Even modest efforts—such as verifying a practice transaction or maintaining several offline copies of your seed word—can avert significant losses.
Verifying your existing wallet configuration and tweaking it as needed will make your cryptocurrency safe yet still available to be sold, spent in DeFi applications, NFTs, or spent on purchases. Ownership is a consequence of having control of your keys combined with good security practice.
The most secure are cold wallets, especially hardware wallets such as Ledger or Trezor. They store all private keys offline and are thus impervious to online hacking attempts. Additional security is provided through multi-signature wallets that require a number of approvals to complete a transaction, which is optimal in high-value accounts.
Yes. Your seed phrase is your master key to reclaim your wallet if lost, broken, or stolen. You lose access to all cryptos held in a non-custodian wallet permanently without it. This is why it is necessary to securely back up your seed phrases.
That is dependent upon your usage and holdings. For small or regular buying/selling amounts, a hot wallet will suffice. But if you have long-term Bitcoin storage or have major Bitcoin holdings, a hardware wallet provides offline protection from hacks and malware that a regular wallet will not.
First of all, make sure that you copy your wallet address properly. Secondly, start a withdrawal from your exchange and enter that address. Always start a small test transfer to make sure that everything is good before transferring higher denominations.
They are if they are downloaded from reputable sources like the App Store and paired with good security practices. Enable device encryption, strong password usage, and two-factor authentication. Avoid unverified or unlicensed apps to reduce malware risk.
The public key can be safely shared to allow others to send to your crypto wallet. It is necessary to spend money, and it proves ownership. The most important thing is to keep the private key safe, as it can move your assets if someone else has access to it.
Most software wallets cost nothing to download and use and are handy to use on a daily basis. Hardware wallets and some of those higher-end services do cost money, but give superior protection to large or long-term stashes.